As today’s technology networks grow ever more complex, the sharing of timely, relevant security information is crucial. Recently, Quokka (formerly Kryptowire) identified multiple security vulnerabilities and privacy issues in Virtual Subscriber Identity Module (vSIM) technology provided by Simo. Simo uses specialized hardware and pre-installed software in certain Android smartphone devices to enable access to mobile data without a traditional SIM card or Wi-Fi connection.
Today, Simo supports numerous telecoms in 135+ countries, with its Simo app showing over 10 million downloads on Google Play. Simo’s software comes pre-installed on its supported devices and Simo uses a “custom” update process to keep its software current. Simo’s software update process is independent of the standard Firmware Over the Air (FOTA) process for the rest of device software. The standard FOTA process for Android devices requires that the update be cryptographically signed with the vendor’s private key, providing a critical authentication layer.
Key Vulnerabilities
Due to multiple flaws in Simo’s software update process, a third-party app that the user downloads and grants write access to external storage, can provide fake Simo software update files that will be treated as authentic to achieve persistent command and code execution as the root user with an SELinux domain of osi (granted various capabilities and full access to the package system service). Prior to our responsible disclosure to Simo and affected Android vendors, all of the devices Simo listed as supported devices on their website were vulnerable to the insecure update vulnerability. On vulnerable versions of Simo software, malicious actors could exploit this local vulnerability to programmatically perform the following actions:
- Achieve persistent code execution by providing an ARM binary that executes at system startup as the root user within the osi SELinux domain
- Execute shell scripts as the root user within the osi SELinux domain
- Install app, uninstall apps, and disable apps
- Grant runtime permissions to apps (including its own app) without user involvement (including permissions with protection levels of dangerous and development)
- Access extensive Personally Identifiable Information (PII) using the granted permissions
- Replace the default “launcher” app with a malicious version that “spoofs” other apps
- Modifying secure settings, including changing the default keyboard to one that has extra keylogging functionality
- Examine the content of active notifications
- Force unload kernel modules
- Sniff network traffic by setting a network proxy
- And more
Simo uses a custom update process that introduces multiple security flaws. It uses an encrypted zip archive containing an update to one of its pre-installed apps (i.e., com.skyroam.silverhelper), a system binary to update, and a shell script to execute. If a co-located app on the device has permission to write to external storage, it can supply a fake software update to run code and commands as the root user within the osi SELinux domain. The 128-bit Advanced Encryption Standard (AES) key cryptographic key that is used to encrypt/decrypt the update file was hard-coded in the /system/bin/osi_bin system binary. The AES key value can easily be extracted from the system binary.
In addition, the update file is transferred using a predetermined file path on external storage without any authentication of the update file, allowing any process with write access to external storage to provide an update file that will be dutifully processed by the /system/bin/osi_bin system binary. Given that access to external storage is a common permission, this represents a major security flaw with serious implications for end users, including those listed above. A malicious actor with this level of permission can manipulate a device and gain access to highly sensitive user information, including text messages, contents of notifications, audio recordings, contact lists, GPS coordinates, call logs, and more. Based on this research, we were granted the following Common Vulnerabilities and Exposures (CVEs): CVE-2021-41848, CVE-2021-41849, and CVE-2021-41850.
PII Transmission
Additionally, we determined that pre-installed Simo software sends specific PII to servers located in China and Germany, at the time of responsible disclosure in late April 2021, including the user’s list of installed apps and the device’s International Mobile Equipment Identity (IMEI) even when the user is not using Simo vSIM services. Alarmingly, all but one of the observed PII transmissions occur without any user involvement and occur by default while running in the background to transmit data.
| URL (without query string) | Initiating Process | Frequency | Notable Data |
| http://log.skyroam.com.cn:9110 /index |
/system/bin/osi_bin | Around every 5 hours | List of installed apps and IMEI are contained in a gzip-compressed plaintext log file that is embedded in a multipart form of an HTTP POST request. |
| http://countly.skyroam.com/i | com.skyroam.silverhelper | Every hour when the device is plugged in to charge | The device IMEI is used as the value to the device_id key in the querystring in a HTTP GET request. |
| https://simo.skyroam.com/simo/ product/commodity/queryExistApp |
com.skyroam.app | Whenever the user clicks the “SIMO” app icon from the launcher | List of user-installed apps and IMEI are sent in the values for the imei and packages keys in a JSON object of an HTTPS POST request. |
The log.skyroam.com.cn domain is one of the primary domains to which the Simo software transmits PII (IMEI and list of installed apps). This occurred over HTTP to a non-standard port of 9110 and occurred by default even when the user does not use Simo’s software. DNS resolution of the log.skyroam.com.cn domain using the dig command, as executed on May 3, 2021, resolved to an IP address of 18.163.199.177. Using MaxMind GeoIP, it estimated that the IP address of 18.163.199.177 is located in Hong Kong, China.
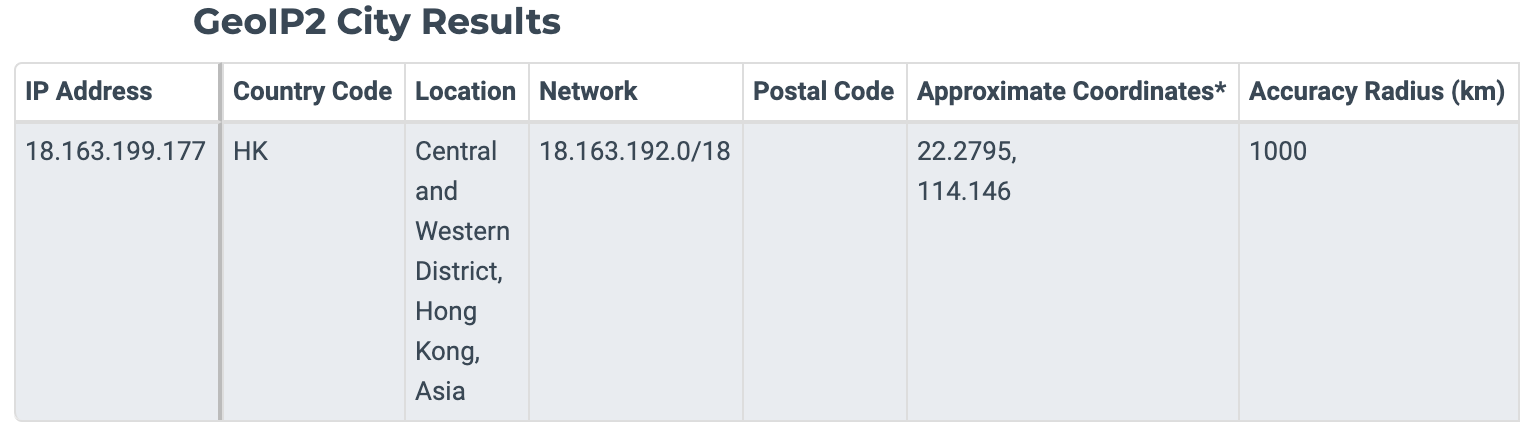
The estimated primary location for receipt of PII information.
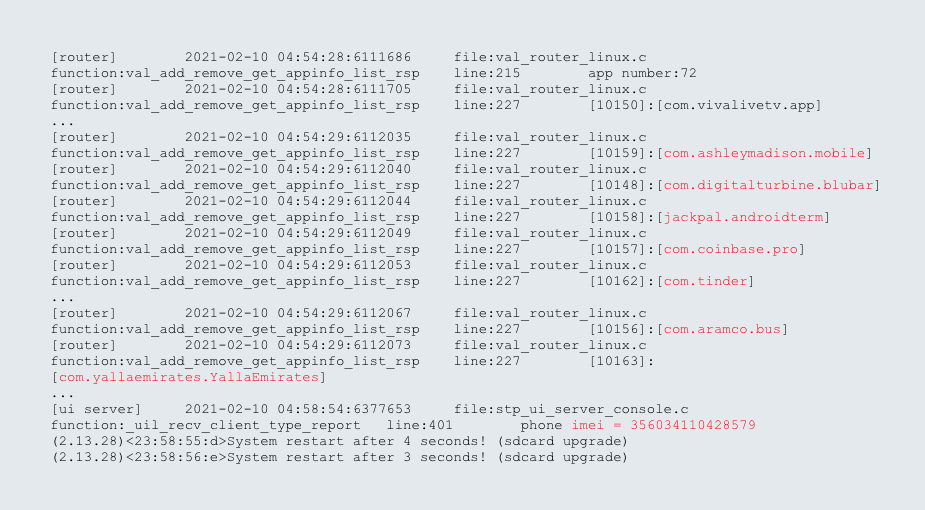
The HTTP POST request from to the log.skyroam.com.cn domain uses a MIME type of multipart/form-data with a boundary of ——WebKitFormBoundaryapMKTQABBP6vWIo0 and the only form data is an encapsulated gzip file containing a log from Simo. The gzip file is not encrypted and can be uncompressed using the standard gunzip command. Some notable lines from the gzip file that were extracted from the HTTP POST request, are provided below. We have provided emphasis on some of the PII (i.e., package names of installed apps and IMEI) by highlighting certain items in red text.
Since our disclosure to Simo and the other affected vendors, the IP address of the log.skyroam.com.cn domain resolves to 35.80.114.254, at the time of writing. In addition, Simo has begun using a new website located at https://www.simo.co/ instead of https://simowireless.com/ that it was using previously, although the previous website can be viewed here. They have also removed all supported devices from their current pages for supported devices, although they can still be viewed on the Simo app on Google Play. At the time of our responsible disclosure and also at the time of writing, the simo.skyroam.com resolves to IP addresses (i.e., 3.69.99.217 and 52.59.84.165) which, at the time of writing, are estimated to be located in Frankfurt, Germany.
In addition to remote exposures of PII, sometimes using HTTP that provides no native encryption, the pre-installed com.skyroam.silverhelper app leaks the device’s IMEI values to system properties at system startup which allows third-party apps that the user installs and grants no permissions to indirectly access non-resettable unique device identifiers that was prohibited in Android 10. This behavior was observed in the BLU G90, BLU G9, and Luna Simo Android devices.
Affected Devices
We dynamically confirmed that the BLU G90, BLU G9, WIKO Tommy 3 Plus, Wiko Tommy 3, and Luna Simo devices were vulnerable to the local insecure update vulnerability. In addition, the Tecno Camon 12 Pro and Tecno Camon 12 had the same SHA-256 message digests of the system binary that introduced the insecure local update vulnerability.
| Insecure Update | PII Transmission |
| Security Vulnerabilities | Privacy Concerns |
|
|
This range of impacted devices is likely larger as Simo’s own listing of devices and does not appear to be exhaustive based on a Facebook post from Simo Nigeria that lists various additional devices.
The table below contains the build fingerprints of the devices that we dynamically verified were vulnerable to insecure update vulnerability and PII exposures.
| Vendor | Model | Build Fingerprint |
| BLU | G90 | BLU/G90/G0310WW:10/QP1A.190711.020/1615191540:user/release-keys |
| BLU/G90/G0310WW:10/QP1A.190711.020/1610513326:user/release-keys | ||
| BLU/G90/G0310WW:10/QP1A.190711.020/1602858033:user/release-keys | ||
| BLU/G90/G0310WW:10/QP1A.190711.020/1592848714:user/release-keys | ||
| BLU/G90/G0310WW:10/QP1A.190711.020/1585383273:user/release-keys | ||
| BLU | G9 | BLU/G9_SR/G0130WW_SR:9/PPR1.180610.011/1573531454:user/release-keys |
| Wiko | Tommy 3 | WIKO/W_K600ID/W_K600:8.1.0/O11019/1547120908:user/release-keys |
| Wiko | Tommy 3 Plus | WIKO/W-V600ID/W-V600:8.1.0/O11019/1539241059:user/release-keys |
| Luna | Simo | ELEVATE/LUNA_G50/LUNA_G50:9/PPR1.180610.011/202001031830:user/release-keys |
Responsible Disclosure
Quokka contacted Simo, Skyroam, BLU, Wiko, Tecno, and Luna to responsibly disclose the vulnerabilities on April 29, 2021 via email to help safeguard the Simo’s end users. Our direct email and phone contact to Simo went unanswered. BLU relayed Simo’s remediation plans via email on June 2, 2021. We will continue to take a proactive, collaborative approach to advancing cybersecurity and keeping end users safe.
Action to Take
To summarize, it is now clear that millions of devices with Simo pre-installed software had security vulnerabilities and privacy issues with serious implications. For end users with devices containing Simo software, we strongly recommend that the user contact Simo and their device vendor to check if they are currently using a vulnerable version of Simo software. The user should also perform any system updates if any are pending.
For device manufacturers, telecommunications carriers, and other industry stakeholders, we urge you to take a proactive, disciplined approach to security and privacy vulnerability detection. Quokka can help you audit your apps, devices, and networks for security and privacy vulnerabilities using our cloud-based, humanless, closed-loop solution. Reach out to the team or follow one of the links below to get started.