Beyond TikTok: A growing mobile security crisis
TikTok’s legal and political turmoil is just one example of a much larger problem. Mobile apps have become hidden threats that pose privacy risks and vulnerabilities everywhere—leaving millions of organizations exposed to attacks they can’t see coming.
With users bypassing official app stores to access restricted apps like TikTok, the risks expand exponentially. These workarounds expose users to unapproved apps, harmful software, and risks from sideloading, leading to serious supply chain software vulnerabilities. Let’s face it—mobile threats are evolving faster than ever, and legacy security just won’t cut it anymore.
What a TikTok ban could mean for security in the workplace
A TikTok ban for national security would undoubtedly alter user behavior, particularly among those willing to take risks to retain access to the app. While this behavior introduces personal risks, the impact on the security teams could be far-reaching.
Many employees use personal devices to access corporate systems, blurring the lines between personal and professional use. When these devices are compromised by malware-ridden versions of TikTok or malicious tools downloaded in the process, they become entry points for cyberattacks. Sensitive corporate data, intellectual property, and even critical infrastructure could be at risk.
Without the vetting processes of Google Play or the Apple App Store, these apps could carry hidden threats–spyware, ransomware, or backdoor access–that infect employees’ devices and, in turn, corporate networks. A single compromised device could create a ripple effect, jeopardizing organizational security and exposing enterprises to costly breaches.
What does the risks of a TikTok ban look like
While a ban on TikTok would require Google and Apple to remove the app from their respective marketplaces, they could also uninstall it remotely from user devices. However, this approach could lead users to seek various workarounds to circumvent the ban. These tactics expose organizations to new vulnerabilities, as users may turn to unofficial sources or employ risky methods to access the app.
- VPN Usage: Users may attempt to access TikTok through VPN connectivity by using built-in device settings or a VPN app. Even though VPNs can bypass geographic restrictions, they can also create security risks by intercepting data on the device or acting as a carrier for mobile malware. Malicious VPNs or poorly configured ones may capture sensitive information such as login credentials and corporate data, leading to data breaches or unauthorized access.
- App Sideloading: third-party app stores may host various versions of TikTok or clones, which can be breeding grounds for malicious software development kits (SDKs). These app stores often lack rigorous security processes, increasing the risk of downloading compromised apps.
- Rooting and Jailbreaking: To sideload an app, users often need to enable features known as jailbreaking (iOS) or rooting (Android), which involves removing built in security protections to accept unknown apps. This practice makes devices more vulnerable to other security threats, such as device takeovers.
- Malware Risks: Users could be tricked into downloading malware masquerading as a replacement for the banned app. It is particularly concerning for Android users who may sideload apps without going through an official marketplace, bypassing security vetting processes and weakening the device’s overall security posture.
These risks are compounded when undertaken by users who may need help understanding the security implications, further increasing the mobile attack surface.
Insights into TikTok’s Inherent Risks: Large User Base, Widespread Security Risk
Now that we understand mobile device and app risks, it’s time to review the risks associated with one of the most widely used apps in the world: TikTok. It’s the fifth most popular social networking app and shows little signs of slowing down.
We examined the risks of TikTok in two key respects: privacy and security.
Permission analysis reveals significant risks
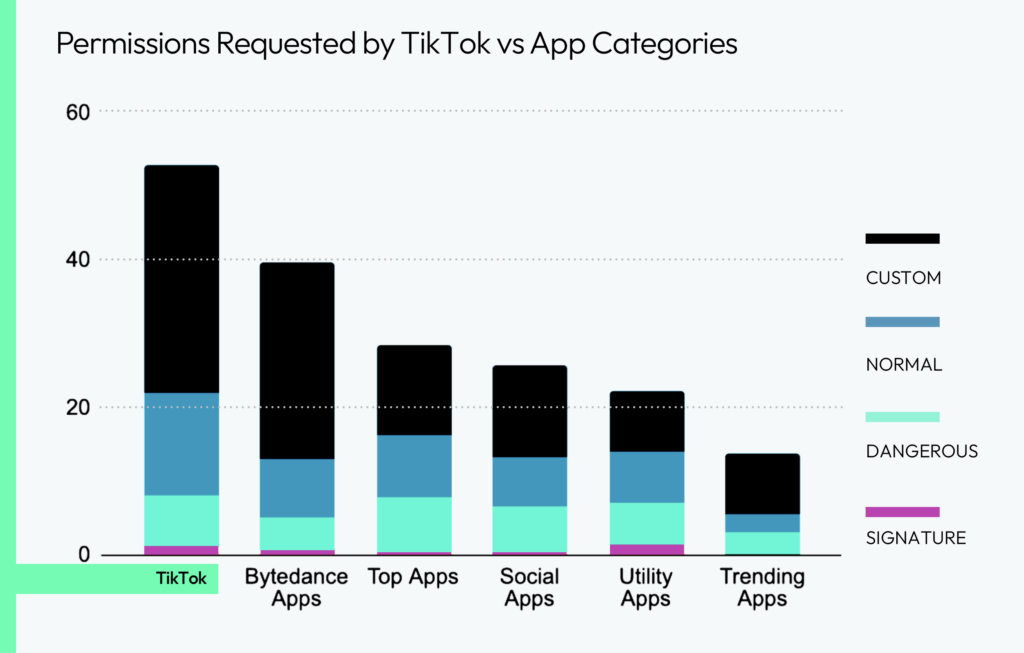
According to Quokka research, TikTok demands an alarming number of permissions from its users, requesting access to twice as much user data as typical social media platforms. ByteDance apps, including TikTok, consistently rank among the most data-hungry in the industry, raising significant privacy concerns.
Our research began in 2019 when we delved into these risks associated with TikTok and uncovered alarming details. We found that TikTok was collecting an excessive amount of data and had permissions allowing it to access information it shouldn’t need, including all data in your notifications. These practices raised serious concerns about user privacy and security, prompting the critical question: Is TikTok the only app engaging in such invasive data collection?
When apps ask for permissions, they request access to specific features or data on your device. Here’s an overview of the privacy risks associated with app permissions:
Privacy risks of app permissions:
- Data collection and sharing:Collecting personal data and sharing it with third parties or using it for targeted advertising without obtaining explicit consent from users.
- Location tracking:Accessing location services can allow apps to track users’ movements, potentially leading to invasive profiling and unwanted surveillance.
- Access to contacts and messages: Accessing contacts or messages can result in unauthorized data sharing, risking user privacy and security, such as phishing.
- Camera and microphone access: Accessing the camera or microphone can record audio or videos without the users’ knowledge, leading to severe privacy violations.
- Device and app usage monitoring: Gathering information about device usage patterns, app activity, and browsing habits, leading to detailed user profiles that can be exploited for various purposes.
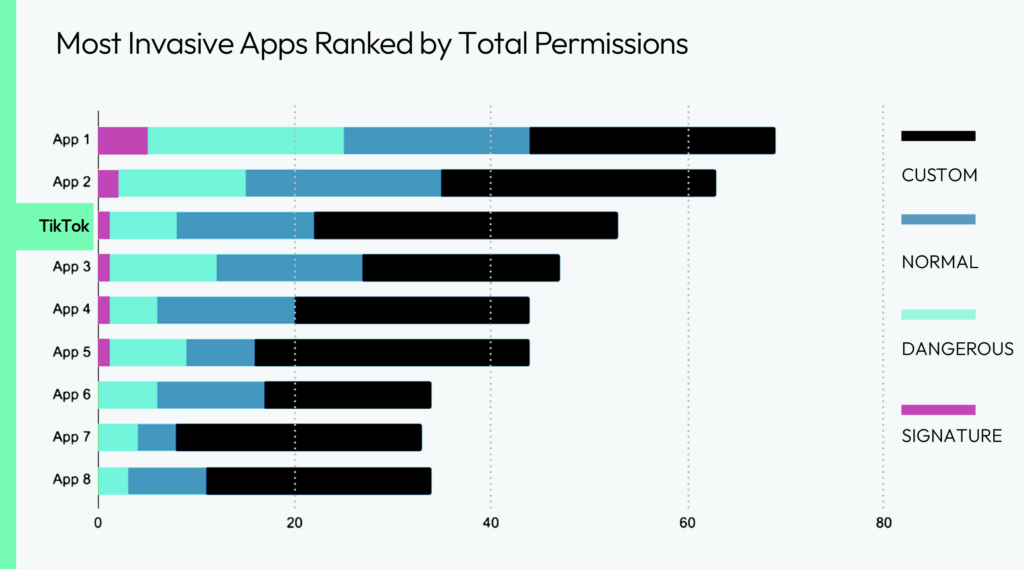
Of the apps analyzed in this research, TikTok is ranked third in the list of the most invasive apps. Even in the short list of the most popular apps in the market, a number of them either exceed or come very close to the level of access that TikTok has. Further, our analysis was only based on a sample set, suggesting that many other apps may match TikTok regarding invasiveness.
Focusing on the TikTok Android app, the version tested, 28.9.4, requests 59 different permissions:
- 25 are standard Android Framework permissions, which are common across many apps.
- 6 are its own custom permissions unique to TikTok, allowing the app to access specific features or data.
- 28 are used to integrate with vendor devices and external libraries, expanding TikTok’s functionality and data access.
These extensive permissions are problematic because they give TikTok access to a wide range of data device features. Some of these permissions require explicit user approval, while others are automatically granted upon installation, leading to privacy concerns.
Security analysis
Threats in the mobile security landscape are multifaceted and require comprehensive evaluation. Our research now shifts from analyzing permissions to examining the security weaknesses within TikTok. Evaluating these security risks is complex and involves considering several factors, including weaknesses in the app’s code, the likelihood of exploitation, and the methods and locations of sharing data.
Our results highlight the risks identified in TikTok’s code, with severity levels categorized as high and medium. This assessment is based on industry standards established by NIST, OWASP, NIAP, and academic research.
Pinpointing overlooked app vulnerabilities
In addition to identifying high and medium risks, we leverage one of our advanced engines to focus on manifest analysis to uncover crucial yet often overlooked vulnerabilities in the app ecosystem.
Previous research conducted by Quokka’s R&D team revealed that many widely used apps contain misconfigurations in their manifest files, potentially resulting in severe security issues. Our tool has detected a significant number of these misconfigurations, highlighting the prevalence of security vulnerabilities across both Google Play and pre-installed apps.
Our engine allows us to analyze each app’s high, medium, and manifest risks. It not only identifies unique vulnerabilities, such as the use of a weak cipher for encrypting data but also measures the total occurrences of each risk. For instance, encrypting data with a weak cipher 100 times presents more risk than doing it only once or twice.
Comparing security risks across apps
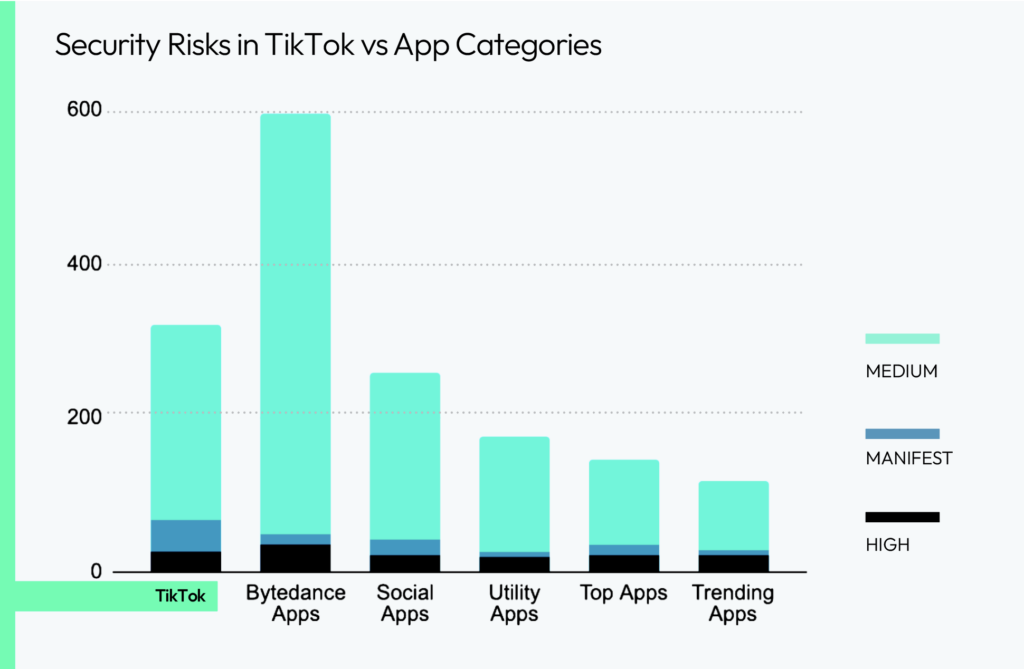
In analyzing popular mobile apps, our research reveals that TikTok poses more security risks than the average social media app. However, it is not the worst offender among the apps reviewed. ByteDance has developed a range of apps that, along with offerings from other developers, collectively present significant security challenges.
Compared to apps in similar categories, TikTok exhibits a higher number of manifest risks compared to medium and high, setting it apart from other apps in the industry. While TikTok’s security profile is concerning, its manifest vulnerabilities are particularly notable and make it stand out among other apps. This underscores the need to prioritize manifest analysis as a crucial part of app security assessments.
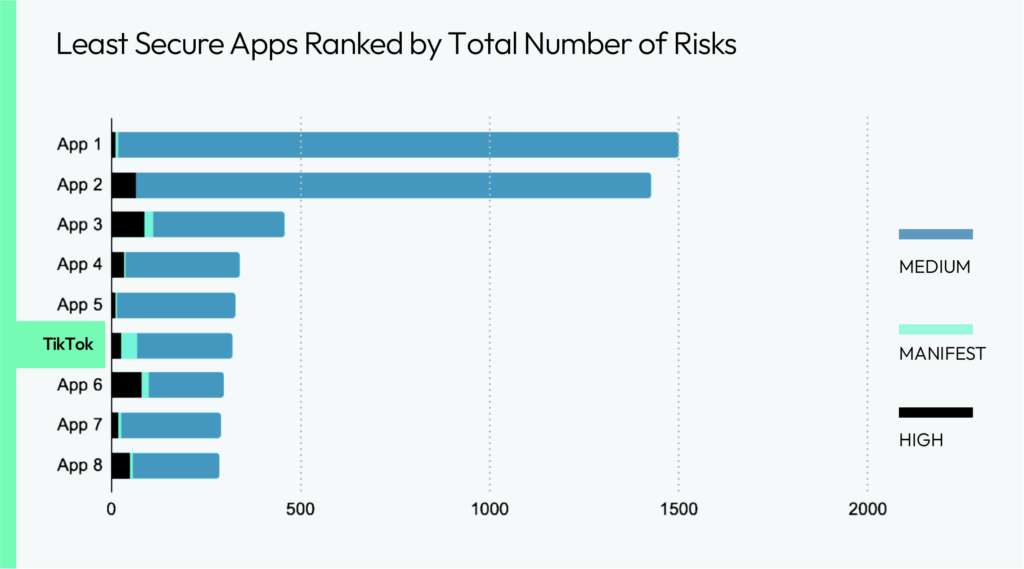
As we shift the focus to examining app security from a different perspective, we reviewed the least secure apps available in the market. TikTok was ranked sixth based on the number of identified risks. This ranking highlights the challenge of balancing security and privacy when it comes to TikTok. While it may be lower on the list of least secure apps, its privacy issues can pose significant threats to business operations, with the potential risk of leaking sensitive employee data and intellectual property.
ByteDance apps and SDK code are prevalent, and problematic
TikTok has been downloaded over one billion times from the Google Play store alone. The broader concern lies with other ByteDance apps, which are available through the same app stores and present even greater risks. When analyzing our database of apps in the market, we found ByteDance’s code in just about every app category.
About 40% of those ByteDance apps had over 100 million downloads each.
ByteDance’s expanding influence through SDKs
Beyond its own apps like CapCut and Lemon8, ByteDance extends its reach through Software Development Kits (SDKs), integrating its code into a wide range of apps available in the app stores.
In our analysis of a sample set of 10,000 Android apps, we looked for direct references with the com.bytedance Group ID. Over 3% of these apps included at least one ByteDance SDK, collectively accounting for over 3.6 billion downloads. These numbers are staggering, demonstrating the extensive reach of ByteDance within just a small sample set.
TikTok itself has over 1 billion downloads, but ByteDance’s code through their SDKs could have 10 to 100 times the number of total downloads. Our findings also show that ByteDance SDKs are primarily concentrated in one app category, with games accounting for about 77% of the total. The remaining 23% are distributed across various other categories, which are outlined below.
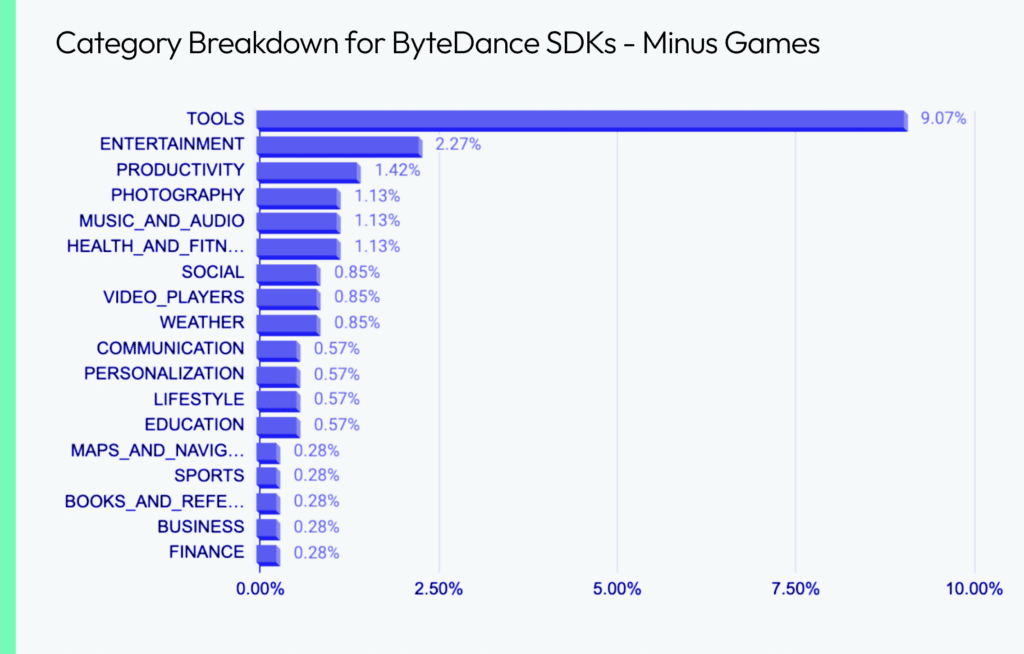
Software development kits: friend or foe?
To understand the security risks of SDKs, it’s important to know their role in app development. Publicly available SDKs are essential for creating Android and iOS apps, allowing developers to quickly and efficiently extend functionality. These pre-built components, tools, and APIs simplify integration, saving developers time and effort compared to coding the entire app from scratch. For instance, SKDs like Google Maps, Firebase, and Facebook offer ready-to-use modules for maps, analytics, social media features, and more — enhancing user experience and accelerating development.
Security risks associated with SDKs
- Weaknesses in code: SDKs may contain vulnerabilities that can be exploited by attackers to compromise the security of the host app and its users.
- Lack of transparency: Developers may not have full visibility into what an SDK does behind the scenes, leading to hidden security and privacy risks.
- Data leakage: SDKs can inadvertently or deliberately leak sensitive data, exposing users to risks such as identity theft and financial fraud.
- Complex supply chains: The inclusion of third-party SDKs complicates the app’s supply chain, making it harder to track and manage security updates.
- Cross-app data sharing: SDKs can facilitate the sharing of data between apps, potentially leading to cross-app tracking and profiling of users.
- Potential for malware: Malicious SDKs can introduce malware into apps, posing significant security threats to users and their devices.
Strategic Measures to Strengthen Mobile Security
- Risk Assessments: Regularly evaluate app security and privacy risks, incorporating behavior analysis to identify suspicious activities or malicious intent. Define acceptable risk thresholds, prioritize vulnerabilities, and assess the potential impact of data breaches.
- App Vetting: Establish a rigorous process to evaluate app permissions, data handling practices, and security before use. Continuously update this process to address emerging threats.
- Mobile App Intelligence: Enhance endpoint security by integrating Mobile App Intelligence solutions with Mobile Device Management (MDM) and Mobile Threat Defense (MTD). These tools can analyze app behavior, detect malicious intent, and enforce proactive, risk-based security measures.
- Mobile App Security Testing: Begin security assessments early in the app development lifecycle to identify and address risks before deployment.
These measures help organizations protect data, users, and devices against evolving mobile threats.
Beyond the Ban: Securing the mobile ecosystem with Quokka
A ban on TikTok doesn’t guarantee a safer mobile ecosystem. Instead, it can introduce new risks, as users turn to unvetted sources, insecure methods, and risky workarounds to access the app. These behaviors expose organizations to vulnerabilities that traditional security tools can’t manage.
At Quokka, we’ve been tackling these challenges for over a decade. In 2018, we were among the first alerting the U.S. government to TikTok’s data vulnerabilities and app collusion.
Our Contextual Mobile Security Intelligence uncovers what others miss—malicious behaviors, colluding apps, privacy risks, and compliance gaps—providing precise, actionable insights to reduce risk and protect your organization. Whether integrated into your infrastructure or deployed as dedicated systems, Quokka ensures clarity in an increasingly complex mobile threat landscape.
With behavior-driven detection, Q-scout identifies hidden threats, streamlines app vetting, and enables swift action to secure your mobile ecosystem—regardless of the operating system (OS). Meanwhile, Q-mast embeds security into the app development lifecycle, conducting comprehensive testing to eliminate vulnerabilities and deliver secure apps from the start.
Mobile security is more than avoiding risks—it’s about proactively safeguarding your ecosystem. With Quokka, you’re equipped to tackle today’s challenges and stay ahead of tomorrow’s threats. Let’s secure your mobile future together—contact us to learn more or schedule a demo today.
December 12, 2024, Update:
TikTok’s time is running out. After a federal court upheld a ruling in December 2024, ByteDance—the app’s parent company—faces a January 2025 deadline to divest its U.S. operations or risk a nationwide ban. Efforts to delay the law have hit a wall, with the Department of Justice urging a U.S. appeals court to reject ByteDance’s emergency motion to block the ruling. Citing national security risks tied to Chinese ownership, the DOJ argues that the threat posed by TikTok’s current structure is too great to ignore.
However, implementing a ban does not automatically create a safer mobile environment. If enforced, users are likely to turn to alternative methods—VPNs, sideloading, and other workarounds—to continue using the app, opening new doors to malicious activity. This creates a critical juncture, not just for TikTok, but also for the broader mobile security landscape.