In today’s mobile-first environment, organizations are increasingly reliant on mobile devices, like smartphones and tablets, to conduct business operations. While Mobile Device Management (MDM) and Mobile Threat Defense (MTD) solutions have become standard tools in enterprise security arsenals, they leave a critical vulnerability exposed: the mobile applications themselves.
Mobile app vetting (MAV) is the missing piece needed for a comprehensive mobile security strategy.
MDM and MTD alone are not enough
MDM solutions play a critical role in ensuring users can access corporate resources on their mobile devices. MDM solutions, such as Microsoft Intune, provide IT teams with centralized control over devices, enabling functions like remote wiping, enforcing encryption, restricting app installations, and monitoring compliance with some security policies. But while MDMs help in managing mobile endpoints, they do not provide comprehensive security.
MTD solutions, such as Microsoft Defender, are also used to protect mobile devices and are usually integrated with MDMs. MTD solutions are vital in helping thwart one of the most common attack vectors: phishing attacks. This is key, because mobile devices present some inherent obstacles in guarding against phishing attacks. For example, a desktop user can hover over a link and inspect the actual URL, so they can spot some of the telltale signs of a suspicious link. Mobile device users aren’t afforded this opportunity. MTD solutions can help guard against users clicking on these risky links.
However, in spite of the value and utility of these MDM and MTD offerings, they leave a big gap. Even after employing both of these solutions, teams struggle to understand security posture and riskiness of mobile apps themselves. These apps can be malicious, harvesting end user data, or colluding with other apps. Through sloppy development practices or the use of third-party code elements, they can introduce a wide range of exploitable vulnerabilities. Even when a user downloads an app for personal use, it isn’t just personal data; corporate access and sensitive information can also be exposed.
Here’s just a few ways sensitive information can be exposed:
- User installs a personal app on a device that’s also used for work—no separation of data
- Clipboard sharing allows the app to read anything copied from Outlook, Teams, and browsers
- SSO/OAuth abuse lets the app access company calendar, contacts, even cloud storage—because the user clicked “Allow”
- Screen reading and background access grab app content, notifications, and messages without obvious signs
- Logs and cache from legit apps get picked up by other apps that scan local storage
These are all a few ways apps can quietly open the door to corporate exposure—without malware, zero days, and users even realizing it.
Better together: Quokka’s mobile app vetting + Microsoft
Mobile apps present an increasingly critical risk to corporate data, user identities, compliance posture, and access controls. That’s why security teams aren’t relying on device policies and endpoint agents—they’re expanding their coverage to include mobile app behavior.
Tools like Microsoft Intune and Defender are critical for managing devices and enforcing protections. For comprehensive coverage, you also need to understand what the apps on the devices are actually doing. Q-scout adds that missing visibility—analyzing mobile apps for risky behavior, data exposure, and compliance vulnerabilities before they become a problem.
Q-scout delivers the in-depth app intelligence and actionable insights you need to protect your organization and mobile workforce from a wider range of mobile app risks. When integrated with Microsoft Intune and Microsoft Defender, organizations are enabled with a range of additional benefits without interruption.
Key benefits of Microsoft with Q-scout
Detect a range of risky mobile apps
Q-scout helps ensure apps running on devices—the software interacting with calendars, contacts, files, and sensitive business data—aren’t quietly introducing risk through embedded third-party code. Most mobile apps heavily rely on third-party SDKs and services, many of which operate with broad permissions and little oversight. With Q-scout, security teams gain visibility into these hidden dependencies and get clear answers:
- Is data being misused?
- Is it leaking information to unapproved regions or vendors?
- Is the app behaving the way it says it does?
Q-scout does extensive types of both static and dynamic analysis that the Quokka team has developed. It also does dynamic analysis on real devices to test how apps are behaving in a user device environment.
Q-scout can detect:
- Shifty apps. Some apps pass store reviews clean, then download new code or enable hidden features post-install. These delayed tactics are used for credential theft, session hijacking, and unauthorized access after the app is already trusted.
- Colluding apps. Two apps share data behind the scenes—one collects, the other exfiltrates. This enables data leakage, location tracking, or policy evasion without triggering standard permission alerts.
- Apps connecting to risky locations. Legit-looking apps may silently communicate with servers in sanctioned countries, unapproved jurisdictions, or cloud providers outside your compliance scope. This creates risk of intellectual property theft, regulatory violations, and nation-state surveillance.
- Zero-day threats. Most mobile security relies on signatures. But modern threats use malicious SDKs, runtime injection, and dynamic code loading to evade detection. Q-scout features a malicious app detection engine designed to detect unknown malware based on what the app does (app behavior)—not what it looks like.
By comparison, MTD solutions like Defender will take signatures of known malware and compare those against apps installed on the device, which only enables detection of malware that has already been identified. Q-scout gathers detailed intelligence and employs a machine learning approach to identify malicious apps based on how they are behaving, including where they’re connecting and how they’re transforming or handling data.
Set enforceable, risk-based app policies
Q-scout gives IT and security teams the evidence and control to decide which apps are allowed, and why. Define clear compliance rules based on behavior, permissions, SDKs, and network activity within the app; instead of relying on the reputation of the app and developer. When an app crosses a red line—such as leaking data to unsanctioned regions, Q-scout provides defensible justification for blocking the apps, backed by detailed, auditable intelligence.
Analyze Mobile App Software Bill of Materials (SBOM)
Mobile app developers continue to grow increasingly reliant on leveraging the code of third-party providers—and at any time there’s a chance that this third-party code may contain an Open SSL, Log4J vulnerability, or outdated ad networks. Beyond checking hashes or CVEs of apps, Q-scout automatically looks at the code that makes up the app, including third-party libraries and SDKs, that are packaged with the app. The solution generates an SBOM on demand for every app that gets pulled from an app store and notifies administrators of which apps have those vulnerable third-party libraries in them.
Pre-vet apps before risk hits the device
TikTok and DeepSeek aren’t edge cases—they’re proof of how fast a mobile app can go viral before anyone knows what’s actually inside. And by the time security catches up, it’s already embedded across thousands of employees’ devices.
With Q-scout, teams can analyze and approve apps “pre-vet” before they ever make it onto user devices, before they are listed in Intune, and before risk is introduced. Trying to do this manually, you could review the app ratings, number of downloads, developer reputations, and various other elements. However, while all those variables may appear fine, the app may still be risky.
Q-scout features a mobile app vetting console that makes it easy for teams to download and inspect an app before it is approved for usage.
Establish continuous application vetting
Analyzing an app yesterday doesn’t help much if a new release is issued today that introduces new security risks. Mobile apps update constantly—new versions introduce risk. Spot checks and annual reviews don’t cut it. That’s how backdoors get in. Q-scout keeps a continuous view of app behavior and risk. When something changes, security teams are alerted. Whether it’s a new API call, an updated third-party library, or shift in outbound traffic, Q-scout flags it immediately.
Agentless deployment
Q-scout performs deep app analysis off-device—no new agents, no extra endpoint load, and no user disruption. Apps are analyzed in the cloud through static and dynamic analysis, including runtime behavior in sandboxed environments. That means you get a clear risk profile before an app ever hits a device. When paired with Microsoft Intune and Defender, Q-Scout enforces policy across managed devices—blocking, alerting, or flagging apps based on real risk, not assumptions.
Scale security visibility
Particularly for any large enterprise, the mix of apps that may reside on any given device is enormous. For example, say you have 1,000 users. There may be 5,000-7,000 different apps used across all those devices and each user will have their own unique mix of apps based on their interests. Q-scout offers the automated scanning capabilities that enable teams to inspect all the apps in play.
How the Microsoft & Q-scout integration works
Q-scout integrates with Microsoft Intune using the Microsoft Graph API, enabling security teams to continuously monitor and assess the mobile apps installed on Intune-managed devices. This integration provides automated ingestion of app inventory from Intune into the Q-scout platform, where each app is analyzed for security and privacy risks. Further, this syncing happens continuously, so as apps are being added, updated, modified, and removed, Q-scout admins are always seeing a current view of apps.
Security teams can:
- Continuously sync with Intune: Q-scout uses the Graph API to regularly pull application metadata—including app identifiers, versioning, publisher details, and device associations from Intune managed endpoints.
- Automated risk assessment: Each app detected in the environment is subjected to both static and dynamic analysis by Q-scout, including inspection of third-party SDKs, permissions, network destinations, and behavioral patterns.
- Policy driven visibility and alerts: When an app fails to meet defined security thresholds, Q-scout generates alerts and risk classifications within the dashboard, enabling administrators to take targeted action.
- Rapid drill down and response: From the Q-scout dashboard, admins can pivot directly into an app’s detailed risk profile without needing to manually correlate device reports or bounce between multiple tools.
This integration ensures that as apps are installed, updated, or removed across the mobile fleet, Q-scout provides a real-time, accurate view or app risk—aligned with enterprise policies and mobile compliance requirements.
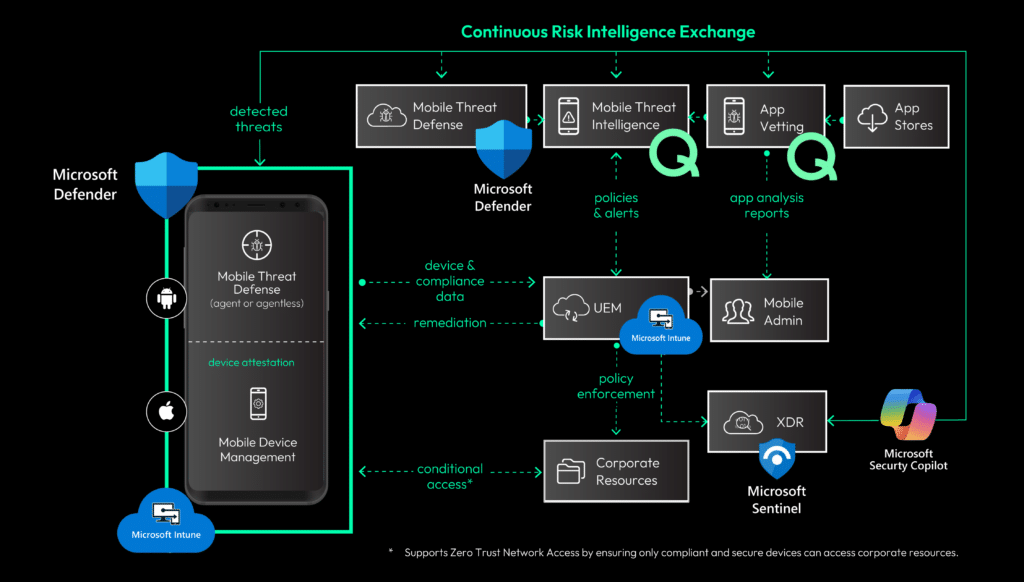
A mobile security ecosystem working in harmony
Mobile security requires a layered approach, and Q-scout fills the critical gap left by traditional MDM and MTD solutions. By providing comprehensive visibility into mobile app risks, automated vetting capabilities, and continuous monitoring of app updates, Q-scout enables organizations to proactively manage the security risks inherent in the thousands of apps across their mobile fleet. The integration with Microsoft Intune and Defender creates a powerful ecosystem where mobile device management, mobile threat defense, and mobile app security work in harmony.
Contact us to get a demo of Q-scout and see how Quokka fits into your mobile security architecture, or watch our “Securing Mobile Endpoints: App Vetting with Quokka & Microsoft Intune” on-demand webinar to learn more.