What are overprivileged apps and why should you care?
In simple terms, overprivileged apps are mobile apps that request far more permissions than they need to function. For example, a flashlight app doesn’t need access to contact lists or location data to function. However, many apps abuse these permissions, which opens the door for them to access sensitive user data, device settings, and functionality.
According to researchers from Cybernews, most apps recently analyzed request permissions to post notifications. While this might seem harmless, malicious apps can exploit a device’s notifications to bombard users with unwanted ads, phishing links, or misinformation. Worse, commercial spyware vendors have used notifications in the past to track users.
The second most requested permission is access to external storage, which apps request read and write access. While necessary for some functions, like uploading media or storing sound files, these permissions pose risks. They could allow apps to access sensitive data, such as your ID photo stored on your device.
How overprivileged apps put your data at risk?
For organizations, overprivileged apps can be a significant threat:
- Data Breaches: By gaining more access than necessary, these apps can expose sensitive user data.
- Malware Exploitation: Overprivileged apps can be exploited by malware, leading to unauthorized access to personal and corporate information.
- Privacy Violations: Excessive permissions can lead to misuse of personal information, compromising user privacy.
These risks can escalate quickly, particularly when organizations allow mobile access to corporate resources without stringent app vetting practices in place.
Steps to protect your mobile devices from overprivileged apps
Whether you’re an individual or part of an organization, staying vigilant against overprivileged apps is critical. Here are a few actionable steps to protect yourself:
1. Avoid Granting Unnecessary Permissions
Only grant the app permissions that are essential to its core function. For example, a photo editing app doesn’t need access to your microphone or contacts. If an app requests more access than necessary, it could be a sign that your data is at risk. Review the Privacy Nutrition Label in the App Store. This label provides a quick overview of the data the app collects and how it may be used, helping you make informed decisions before granting permissions.
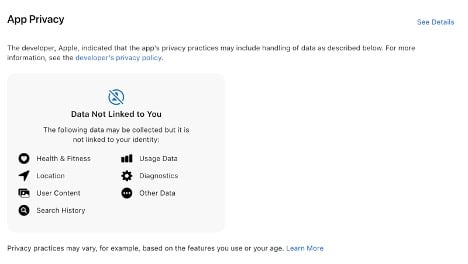
Source: Apple
2. Limit Permissions Based on Use
For iOS users, apps can request additional permissions while in use. Take advantage of this feature to limit access to your data when apps aren’t actively in use. This ensures minimal risk while keeping your personal information safe.
3. Conduct Regular App Hygiene Check-ins
Perform regular reviews of your installed apps and their permissions:
- Remove Unused Apps: Delete any apps you no longer use to reduce potential access to your data.
- Review Permissions: Check if frequently used apps have excessive permissions, and scale them back if necessary.
4. Reach out to IT for Mobile Security
If you’re part of an organization, request a mobile security solution from your IT department. This can help you identify and mitigate security risks posed by overprivileged apps.
By integrating regular app hygiene into your mobile security practices, you’ll enhance your data protection and ensure that apps have only the access they truly need.
Secure Your Organization with Mobile App Vetting
For organizations, understanding and managing overprivileged apps is essential for maintaining a secure mobile ecosystem. Implementing a comprehensive mobile endpoint solution will help protect corporate data, ensure compliance, and minimize the risks associated with excessive permissions.
Looking to protect your organization from mobile security threats? Explore Quokka Q-scout mobile endpoint security, designed to block overprivileged apps and safeguard your data.