Are you reading this blog on a smartphone? Thanks to modern technology, users may view their smartphone as an abstract, rectangular computer that facilitates many of life’s daily tasks and connects us with the world. For a smartphone to be of much use to the user (beyond what its physical form provides), it must come pre-loaded with various software that allows users to perform tasks. Smartphones require an Operating System (OS) which provides an execution environment for applications (subsequently referred to as “apps”) to run. The two most popular mobile OSs in the world are Android and iOS. In addition to the OS software, the manufacturer of a mobile device includes a curated selection of pre-installed software that provides a foundation from which to extend the smartphone’s functionality through the downloading of additional apps, also referred to as third-party apps.
There are pre-installed apps you are likely familiar with and use often such as the apps that provide the functionality to send text messages, browse the internet, make phone calls, take photos, and download additional apps. In addition to the apps that provide these useful functionalities, there are also pre-installed apps that you do not see (and therefore typically do not use) since they do not have icons in the launcher that allows you to start them, rendering them as hidden to the user. Hiding these apps from the user is warranted in many cases as an uninformed user might make unnecessary changes using the apps that impact the smartphone in a negative way. Some of these hidden apps have high levels of privileges, where some even run with the same level of privilege as the system itself. The pre-installed apps generally cannot be uninstalled; this is important since this prevents a user from unknowingly removing an app that provides an important service, potentially a core one, which could negatively impact usability or security. Imagine if you accidentally uninstalled the Settings app. On the other hand, if one of these pre-installed apps has a security weakness, then the user may not be able to disable or uninstall the vulnerable app themselves.
Both pre-installed apps and third-party apps execute within a sandbox, provided by the Android OS, that isolates and protects their files and resources from other apps. Despite the app sandbox, an app can facilitate communication between itself and other apps co-located on the smartphone through legitimate means that are provided by the Android OS. This inter-app communication provides a rich user experience as it allows deep integration, data sharing, and ease of use for the user. When opening avenues for communication amongst apps, great care should be taken to try to prevent them from being abused by bad actors. Due to the complexity of modern mobile software, there is a risk that app developers fail to implement best security practices and unintentionally expose their privileged capabilities and sensitive data to other apps that have less privileges. For example, this may manifest as an app failing to perform access control at the interface boundary of a software component that performs a security-sensitive task. Failing to enforce access control can allow entities to access capabilities to perform specific actions and access sensitive data without being authorized to do so.
Due to the severity of potential security issues in pre-installed software, we analyzed numerous mobile devices to assess their security posture and examine how mistakes in their software could potentially be abused by attackers. In our analysis, we solely focused on smartphones running the Android OS as it is the most popular mobile OS in the world with a global market share of 70.8%.1 Android has a mobile OS market share of 42.5% in the United States.2 We specifically focused our analysis on prepaid Android smartphones which are smartphones that you pay for in full at the time of purchase and generally use a prepaid service plan where its duration is one to a few months. Some prepaid smartphones can cost as little as $50. All of the major American carriers offer prepaid smartphones and prepaid service plans. We undertook a similar analysis of prepaid Android carrier devices five years ago and demonstrated that there were concrete security issues in the prepaid Android smartphones we examined which was presented at the DEF CON 26 conference in 2018, you can read the technical paper here.3
We re-examined the same topic this year, providing a longitudinal perspective, and discovered that concrete security issues still persist in prepaid Android carrier devices. Our findings will be presented at the DEF CON 31 conference in August 2023.4 In total, we examined 21 prepaid Android carrier devices, covering all of the major American carriers to assess the security of their pre-installed software. Table 1 provides the list of the 21 smartphones we examined, providing the carrier, vendor, and model for each. We tried to have similar coverage among the various carriers, although Tracfone is quite well-represented since they are a major player in the Android prepaid market.
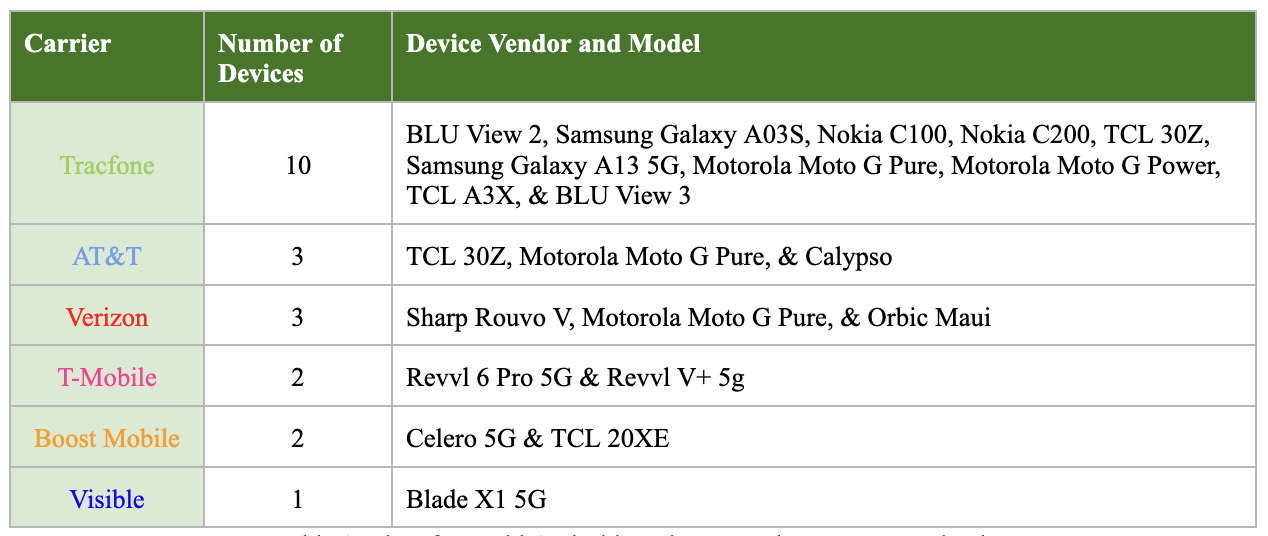
Table 1. List of prepaid Android carrier smartphones we examined.
For each of these 21 Android smartphones, a number of entities provide software components that ultimately comprise the final software build that runs on the smartphone. Some of these entities that furnish the software are the Android Open Source Project (AOSP), chipset manufacturers, hardware manufacturers, carriers, vendors, and vendor partners. AOSP is the core Android code that Google provides, which vendors modify to differentiate their offerings in the smartphone market. AOSP, as the acronym states, is open source software and is easily accessible online.5 While vendors may make direct modifications to AOSP code, they generally also include numerous pre-installed apps that the user may or may not find useful. These can range from popular apps such as Netflix and Facebook to apps you have likely never heard of such as engineering and factory apps that allow an operator to test hardware and software functionalities from a central location. These more obscure apps are likely to never be used by the user, as they do not have icons in the launcher, and arguably provide little utility on the device in general.
While Google performs security vetting of Android apps that are listed on Google Play, malicious apps that have slipped by in the past.6 While paying close attention to the permissions an app requests is very important and provides you with an approximation of what the app is capable of doing, a malicious app may also turn to its environment to take advantage of insecure interfaces of co-located software to illicitly increase its capabilities to escalate its privileges. Therefore, the permissions an app requests may not be a complete listing of what an app can potentially do, as it can utilize insecure software in its environment to indirectly perform actions that it does not have the privileges to perform directly, manifesting as instances of the confused deputy problem.7 In other cases we observed, pre-loaded software obtains sensitive data and makes it accessible, using one mechanism or another, to co-located apps without performing the requisite access control checks. This creates a leakage of sensitive data where malicious apps can monitor and harvest this sensitive data if they are aware of where to obtain it. So while it may appear that a mobile app’s capabilities are circumscribed by the permissions it requests, an app can use underhanded techniques to expand them in a way that is not reflected solely in its list of requested permissions.
A manifest file is required for all Android apps and serves somewhat like a specification for the app’s identity, software components, permissions, required hardware features, and much more.8 Android uses a permission model where apps declare the permissions they want in their manifest files. For example, if an app needs to connect to the internet, the app developer declares this fact in its manifest file by requesting the permission named “android.permission.INTERNET“, entitling the app to access the internet. A more detailed overview of Android permissions is provided here.9 A permission is like a credential that allows it to perform an associated action (e.g. the “android.permission.BLUETOOTH” permission allows an app to connect to other Bluetooth-enabled devices) or get access to a specific type of data (e.g., the “android.permission.READ_SMS” permission allows an app to obtain read access to the user’s text messages).
For sensitive permissions (also referred to as dangerous permissions), such as the “android.permission.READ_SMS” permission, the user gets to grant or deny the app’s request for sensitive permissions by clicking the desired option in a GUI dialog. Sensitive permissions are denied by default until the user grants them to the requesting app. This is the standard permission-granting model for Android apps where the level of capabilities and access to user data (made accessible through permissions) is proportional to how much the user trusts that an app will not abuse its permissions. Pre-installed apps are generally considered to be more trustworthy, since they are handpicked by the smartphone’s manufacturer, so they can request and be granted a special set of permissions that are not directly accessible to the third-party apps that the user downloads. The capabilities and data made accessible through the permissions made only available to pre-installed apps can still be leaked to third-party apps through insecure interfaces.
There is a risk that a third-party app you download is aware of security-related software vulnerabilities in your pre-installed software, comprising the Android software stack, and exploits these vulnerabilities to obtain an elevated level of access to capabilities and sensitive data, exposing the user to potential harm. The primary mechanism for Android apps to communicate within itself and externally with other apps is by using a mechanism called an Intent message.10 An Intent is like a message with destination information (i.e., which software component(s) should receive the message) and potentially embedded data stored as key-value pairs. All but the most non-trivial apps use Intents for communication. This fundamental form of communication is not inherently malicious as it is provided by the Android platform itself. Without knowing a-priori that a specific destination component has an exploitable software flaw or employing another method to classify the communication as potentially malicious based on some set of features, it can be difficult to detect that a software component is being exploited by being sent crafted Intent messages to its vulnerable app interfaces.
In the instances of insecure pre-loaded software on the prepaid Android carrier devices we discovered, we demonstrate that a third-party app that requests 0 to 1 permissions in its manifest file, can achieve a range of capabilities without proper authorization by leveraging insecure co-located, pre-installed software. The exact set of illicit capabilities that an app can achieve depends on which Android device (and thus the software it contains) it is executing on. Table 2 provides a high-level summary on the prevalence of vulnerabilities and the percentage of devices impacted based on the presence of the vulnerability in the 21 prepaid Android carrier devices we examined.
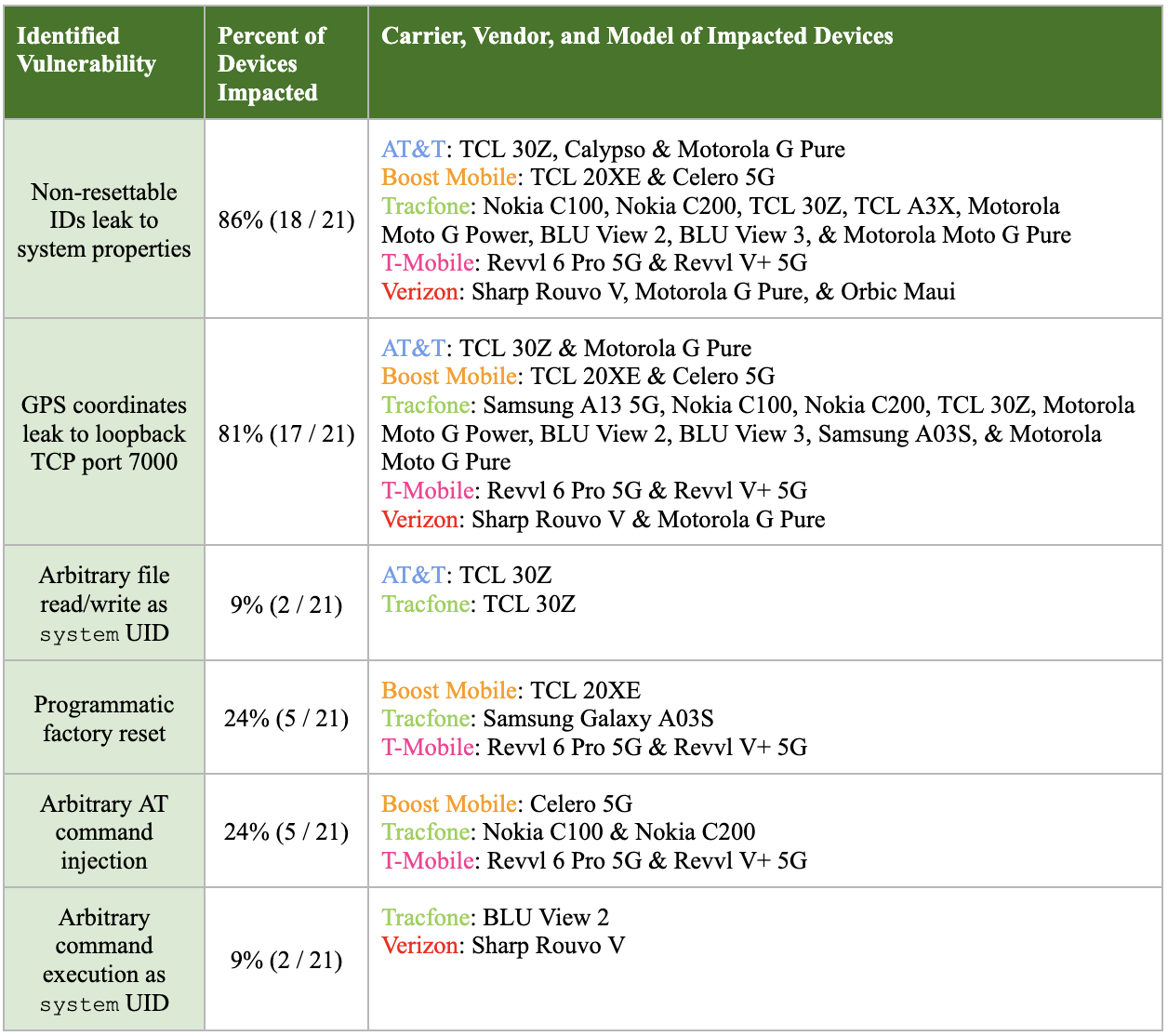
Table 2. Prevalence of vulnerability types discovered in prepaid Android carrier devices.
Some of the vulnerabilities we discovered may have technical names that may be unfamiliar, so we provide a more detailed explanation of the vulnerabilities and what they can potentially entail for the user in Table 3.
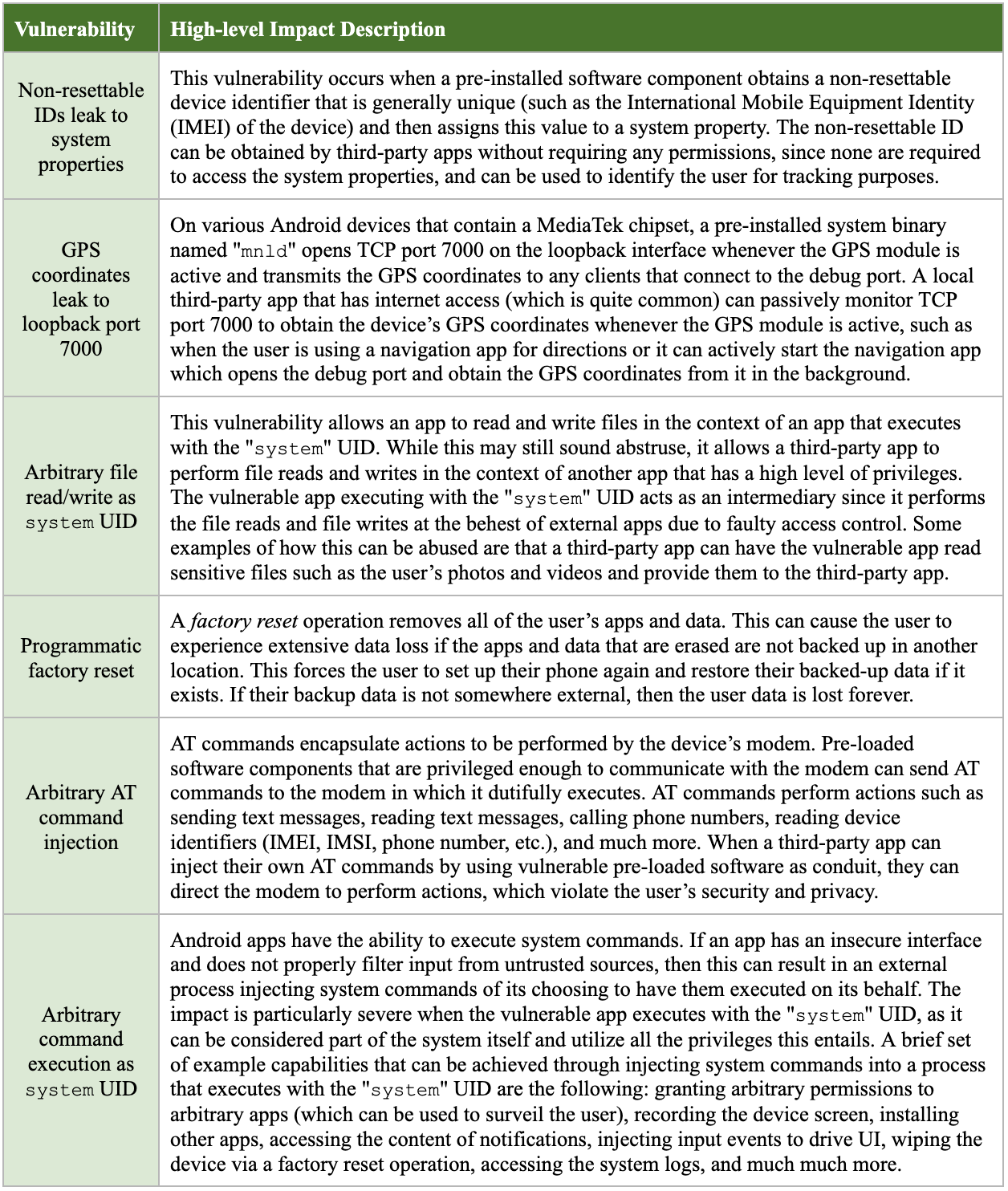
Table 3. Vulnerability descriptions and their potential impact to the user.
So at this point, you may be wondering how to protect the personal data on your device. A good place to start is by educating yourself on the threats and risks associated with mobile devices.11 In general, it is critical to keep all of your software up to date as each update may contain security fixes that patch known software vulnerabilities. If you are an app developer, then understanding and implementing the security best practices can help these flaws from being introduced in the first place.12 In addition to discovering these vulnerabilities, Quokka also helps users detect if their devices are impacted by these vulnerabilities. Quokka offers a Personal Device Management (PDM) solution named Q-Scout that is available for free for Android that can detect if your device is impacted by these vulnerabilities.13 Q-Scout is also available for free for iOS devices.14
1 https://gs.statcounter.com/os-market-share/mobile/worldwide
2 https://gs.statcounter.com/os-market-share/mobile/united-states-of-america
3 https://www.youtube.com/watch?v=R2brQvQeTvM
4 https://info.defcon.org/event/?id=50797
5 https://cs.android.com/
6 https://www.bleepingcomputer.com/news/security/android-malware-infiltrates-60-google-play-apps-with-100m-installs/
7 https://en.wikipedia.org/wiki/Confused_deputy_problem
8 https://developer.android.com/guide/topics/manifest/manifest-intro
9 https://developer.android.com/guide/topics/permissions/overview
10 https://developer.android.com/guide/components/intents-filters
11 https://www.cisa.gov/sites/default/files/publications/cyber_threats-to_mobile_phones.pdf
12 https://developer.android.com/topic/security/best-practices
13 https://play.google.com/store/apps/details?id=com.kryptowire.matador
14 https://apps.apple.com/us/app/q-scout/id1634815152